Getting rid of Putty – ssh history
for ((i=1; i<=5; i++)); do history -d $(history 1 | awk '{print $1}'); done
to get rid of the last 5 lines / commands

for ((i=1; i<=5; i++)); do history -d $(history 1 | awk '{print $1}'); done
to get rid of the last 5 lines / commands
We added a loop grid and a taxonomy filter for our products but when clicked on any filter – product tag in our case – there was no results. Query monitor gave the error : Unknown column ‘t.term_order’ in ‘order clause’ But the default wp _terms table did not have a term_order column anyway. So…

While optimizing our MySQL server we noticed our mysqld.log was huge in size – 1GB+ – and it was filling every moment with the below message: [Warning] [MY-013360] [Server] Plugin mysql_native_password reported: ”mysql_native_password’ is deprecated and will be removed in a future release. Please use caching_sha2_password instead’ Below article explains the issue https://support.cpanel.net/hc/en-us/articles/16550190886935-MySQL-log-warning-mysql-native-password-is-deprecated-and-will-be-removed-in-a-future-release But it…
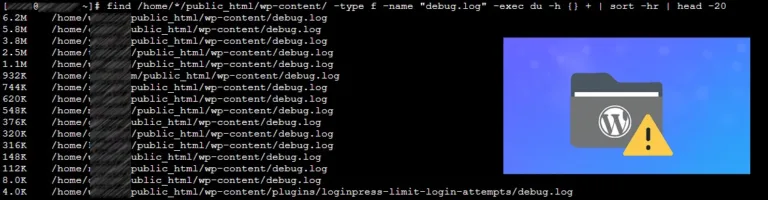
Why debug.log Files Matter Performance impact: Large log files can eat up disk space and slow down file operations. Backup bloat: If your backups include debug.log, they can become unnecessarily large. Security risk: Debug logs may contain sensitive paths, plugin names, or even database queries. If exposed publicly, attackers could use this information. Maintenance signal:…
We wanted to display product variations as selectable boxes rather than dropdown / select. So we needed to use a modified variable.php to modify the variations form accordingly under: /public_html/wp-content/themes/child-theme/woocommerce/single-product/add-to-cart/variable.php We thought a WC template file under child theme would work for sure in terms of hierarchy it should override wc default and the parent…
We were promoting our codes with capital letters as a style choice But while the code “burhi” worked the code BURHİ did not because Turkish, “i” and “İ” are considered as different characters, and the lowercase of “İ” is “i”, not “ı”. T. The code should work for other international accented diacritic characters like umlauts
Moving a WordPress site from your main domain to a subdirectory (like from site.com to site.com/mirror/) is a common task for developers working on staging environments or site redesigns. However, simply copying files isn’t enough—you need to update your database to reflect the new URL structure. Here’s your comprehensive guide to making this transition smoothly….